KAIST
BREAKTHROUGHS
Research Webzine of the KAIST College of Engineering since 2014
Spring 2025 Vol. 24Bug hunting in JavaScript web applications in the wild
SAFE, a Scalable Analysis Framework for ECMAScript, can analyze JavaScript web applications in the wild automatically to detect real-world bugs efficiently and precisely.
Article | Fall 2014
The JavaScript programming language, originally developed as a simple scripting language, is now the language of choice for web applications. All the top 100 most popular websites according to the Alexa list (http://www.alexa.com/topsites) use JavaScript, and various platforms, including mobile devices and smart TVs, use JavaScript extensively. However, JavaScript has many quirky features that often lead to security and privacy vulnerabilities.
On top of that, web application developers should understand complex interactions between multiple components of web applications written in different languages. Indeed, many JavaScript errors originate from using APIs between various components incorrectly.
The Programming Language Research Group of Prof. Sukyoung Ryu in the Department of Computer Science is working on analyzing JavaScript web applications in the wild to find and fix real-world bugs. Collaborating with researchers in industry including Samsung Electronics and S-Core, the team has been developing SAFE, a Scalable Analysis Framework for ECMAScript, and has made it publicly available. SAFE analyzes JavaScript web applications and library APIs automatically and detects possible errors in the web applications precisely.
Instead of trying to infer programmers’ intention from extremely dynamic JavaScript programs or from closed-source platform-specific libraries, SAFE utilizes library specifications written in various interface description languages, such as Web IDL and TypeScript, to analyze interactions between multiple components automatically, precisely, and efficiently. While the JavaScript language semantics allows one to call a function defined with some parameters without any arguments, platform developers require application writers to provide the exact number of arguments. Because library functions in APIs expose their intended semantics clearly to web application developers, unlike pure JavaScript functions, SAFE can detect incorrect uses of APIs precisely. Also, SAFE enhances analysis precision by connecting missing execution flows between open-source JavaScript applications and closed-source platform functions via modeling asynchronous semantics by events and callback functions.
In the course of developing SAFE, the team found previously undetected bugs in widely used applications including a SunSpider JavaScript benchmark and http://www.wikipedia.org/. SAFE detected representative misuses of web APIs identified by software quality assurance engineers in real-world JavaScript web applications. It even detected inconsistencies in web API specifications and found real bugs in examples of them. SAFE is currently being used by colleagues in Seoul National University, University of Illinois at Urbana-Champaign, and Hong Kong University of Science and Technology, as well as by industrial partners, and the team won the Google Faculty Research Award for their work in 2013.
URL: https://github.com/sukyoung/safe
This work is supported in part by the NRF of Korea (Grants NRF-2014R1A2A2A01003235 and NRF- 2008-0062609), Samsung Electronics, S-Core, and Google, and will be presented at The 22nd ACM SIGSOFT International Symposium on the Foundations of Software Engineering (FSE 2014), November 2014.
Most Popular

When and why do graph neural networks become powerful?
Read more
Smart Warnings: LLM-enabled personalized driver assistance
Read more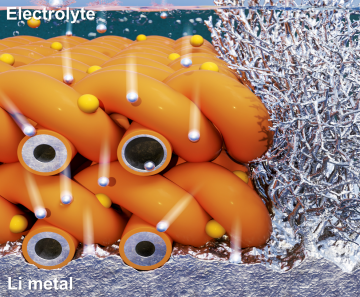
Extending the lifespan of next-generation lithium metal batteries with water
Read more
Professor Ki-Uk Kyung’s research team develops soft shape-morphing actuator capable of rapid 3D transformations
Read more
Oxynizer: Non-electric oxygen generator for developing countries
Read more
