KAIST
BREAKTHROUGHS
Research Webzine of the KAIST College of Engineering since 2014
Spring 2025 Vol. 24Puppetizing cellular data accounting
A close-up measurement of cellular network operators reveals vulnerabilities in the traffic accounting system that allow attackers to arbitrarily control data billing.
Article | Spring 2015
A KAIST research team led by Professors KyoungSoo Park and Yongdae Kim has found that a modern cellular network can be easily manipulated to either overcharge a user or use the Internet traffic for free.
The attack relies on retransmission of a packet, which is a unit of data delivered over the network. To send a content (e.g., email, image, video clips) via the internet, the content has to be divided into small units called packets, and the packets are delivered to the destination independently. Packet retransmission is a fundamental transport-layer feature (e.g., TCP) that ensures reliable data transfer between two communicating hosts (e.g., a smartphone and web server). When a packet fails to reach the destination due to poor network conditions, the sender retransmits the same packet until the receiver acknowledges that it has received it.
Interestingly, when it comes to cellular data accounting, retransmission creates an important policy issue. Cellular network operators might argue that all retransmitted packets should be charged since they consume the resources of their infrastructure. In contrast, the cellular subscribers might want to pay only for the application data by subtracting the amount of retransmission. The real-world measurements by the team reveal that cellular operators in most countries (e.g., US, China England, Germany, Spain) charge for retransmission while those in South Korea do not.
Regardless of the policies, however, retransmission can be abused to manipulate the cellular traffic accounting. First, cellular operators that charge for retransmissions are vulnerable to a “usage-inflation” attack, where the attacker can arbitrarily inflate the usage of a target subscriber by intentionally retransmitting packets, even without actual packet loss. This attack is powerful since it does not require compromising the client. As long as the user is redirected to a malicious server (via ads or phishing messages), the attacker can inject any number of retransmission packets. The research team has shown that a single attacker can cause a user to be overcharged for 1 GB within 10 minutes.
Second, cellular operators that do not charge for retransmissions could be vulnerable to a “free-riding” attack, where the subscriber avoids data billing by masquerading normal packets as retransmissions. In this attack, the subscriber colludes with a proxy that communicates with a server on behalf of the client. When normal data packets from the server arrive at the proxy, the proxy fabricates the packet headers (packet metadata) to masquerade them as retransmitted packets. These packets are then forwarded to the client via a cellular network where the accounting system considers them as retransmissions and does not charge for the data.
The work on real-world implementations of “usage-inflation” and “free-riding” attacks as well as the defense mechanism were presented at the 2014 Network and Distributed System Security Symposium (NDSS), a top venue in network security. An earlier version of the research that found the vulnerabilities of cellular operators was published in the ACM HotMobile workshop and received the best paper award in the ACM S3 conference. All cellular operators in South Korea were notified of this attack before the publications were released. More details of the work can be found at http://abacus.kaist.edu/.
Additional information can be found from: http://abacus.kaist.edu/
Most Popular

When and why do graph neural networks become powerful?
Read more
Smart Warnings: LLM-enabled personalized driver assistance
Read more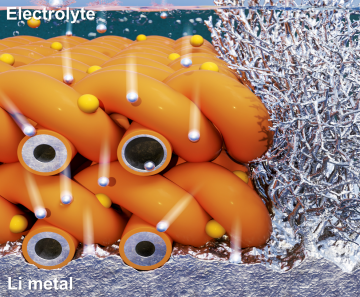
Extending the lifespan of next-generation lithium metal batteries with water
Read more
Professor Ki-Uk Kyung’s research team develops soft shape-morphing actuator capable of rapid 3D transformations
Read more
Oxynizer: Non-electric oxygen generator for developing countries
Read more

